Note: A 2022 tutorial on the many aspects of IPv6 can be found in this All Things TECH IPv6 on Windows article.
Internet Protocol version 6 (IPv6) is enabled by default in all versions of Microsoft Windows 8 or later and Server versions released in 2013 or later. Unless explicitly disabled, IPv6 will also be enabled (or reenabled) upon upgrading to any version of Windows 8 or later or Server versions released in 2013 or later. If you want to disable IPv6, the following five methods are available.
Caution: In this February 2011 Why you should leave IPv6 alone article, Microsoft recommends that IPv6 not be completely disabled, but instead that the IPv6-tunneling interfaces be disabled.
Method 1. (Traditional method used by all Windows versions.) In the Network Connections folder of the Network and Sharing Center on the Control Panel, obtain properties on all of your connections and adapters and clear the check box next to the Internet Protocol version 6 (TCP/IPv6) component in the list under This connection uses the following items. This method can be used to disable IPv6 on each network interface and connection, but does not disable IPv6-tunneling interfaces nor the IPv6 loopback interface.
Method 2. Run PowerShell as an Administrator. Run the cmdlet
Get-NetAdapterBinding
to list all Network Adapters on the computer and the state of the ms_tcpip6 ComponentID for each Network Adapter. For each Network Adapter for which the ComponentID ms_tcpip6 shows Enabled = True, run the cmdlet
Set-NetAdapterBinding -Name “Network Adapter Name” –ComponentID ms_tcpip6 –Enabled $False
To disable IPv6 for all Network Adapters on the system with a single command, use
Set-NetAdapterBinding -Name “*” –ComponentID ms_tcpip6 –Enabled $False
An alternative cmdlet to the above command is the command
Disable-NetAdapterBinding -Name “*” –ComponentID ms_tcpip6
The netsh command line interface which was used in Windows 7 and Server 2008 to configure and manage TCP/IP configurations still exists, but Microsoft recommends that you transition to Powershell. In future updates of Windows, Microsoft may remove the netsh functionality.l
Method 3. Use either (a) the wizard or (b) follow the directions for modifying the registry in this article on the learn.microsoft.com website. (As noted in that article, after following these directions for modifying the registry, method 1 can no longer be used.)
Method 4. Search for the regedit app and Run as Administrator (older than but similar to method 3(b) above.
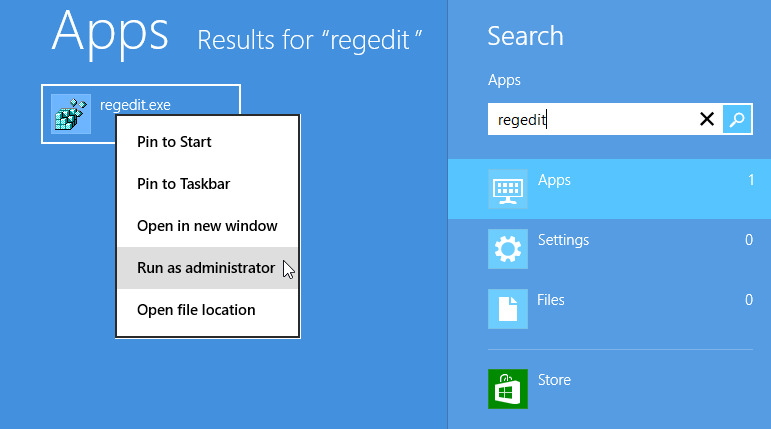 atitle="Windows 10 “regedit” search" hr" re"><i" sr" al" wi" he"></" />" />"
atitle="Windows 10 “regedit” search" hr" re"><i" sr" al" wi" he"></" />" />"
Windows 8 “regedit” search Windows 10, 11 “regedit” search
If it doesn’t already exist, add the following registry value (DWORD type):
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters\DisabledComponents
DisabledComponents will be set to 0x0 by default. Set it to 0xFF to disable IPv6 on all your network interfaces, connections, and IPv6 tunneling interfaces. You must restart the computer for this registry value to take effect.
Note: In line with the Microsoft recommendation mentioned at the beginning of this article, it is suggested that DisabledComponents be set to 0xAF rather than 0xFF.
When DisabledComponents exists and a DisabledComponents bit is set, it overrides any settings established by methods 1 and 2. The DisabledComponents registry value is a bit mask that controls the following series of flags, starting with the low order bit (Bit 0):
- Bit 0 Set to 1 to disable all IPv6 tunnel interfaces, including ISATAP, 6to4, and Teredo tunnels. Default value is 0.
- Bit 1 Set to 1 to disable all 6to4-based interfaces. Default value is 0.
- Bit 2 Set to 1 to disable all ISATAP-based interfaces. Default value is 0.
- Bit 3 Set to 1 to disable all Teredo-based interfaces. Default value is 0.
- Bit 4 Set to 1 to disable IPv6 over all non-tunnel interfaces, including LAN interfaces and Point-to-Point Protocol (PPP)-based interfaces. Default value is 0.
- Bit 5 Set to 1 to modify the default prefix policy table to prefer IPv4 to IPv6 when attempting connections. Default value is 0.
- Bit 6 This bit was reserved for future use up until Windows Server 2019. Set to 1 to disable all CP-based interfaces. Default value is 0.
- Bit 7 Set to 1 to disable all IP-TPS-based interfaces. Default value is 0.
To determine the value of DisabledComponents for a specific set of bits, construct a binary number consisting of the bits and their values in their correct position and convert the resulting number to hexadecimal. For example, if you want to disable 6to4 interfaces, disable Teredo interfaces, and prefer IPv4 to IPv6, you would construct the following binary number: 00101010. When converted to hexadecimal, the value of DisabledComponents is 0x2A.
Method 5. Issue the following command line as an Administrator:
reg add hklm\system\currentcontrolset\services\tcpip6\parameters /v DisabledComponents /t
REG DWORD /d 0xFF
The above registry entry should already exist. If it doesn't, create it.
Note: in line with the Microsoft recommendation mentioned at the beginning of this article, it is suggested that DisabledComponents be set to 0xBF rather than 0xFF.
